Attachmate Reflection for Secure IT
Reflection for Secure IT Server uses the SSH protocol to provide secure file transfer and remote administration services for both Windows & UNIX environments. Reflection for Secure IT family of SSH clients and servers for Windows and UNIX—all designed to protect data in motion.
Overview:
- Replace nonsecure Telnet and FTP with a secure, encrypted alternative.
- Secure remote administration of critical servers, even over untrusted networks.
- Enhance administrative control with support for Post Transfer Actions and ProcessPriority.
- Safely transmit sensitive data and ensure that transfers are completed.
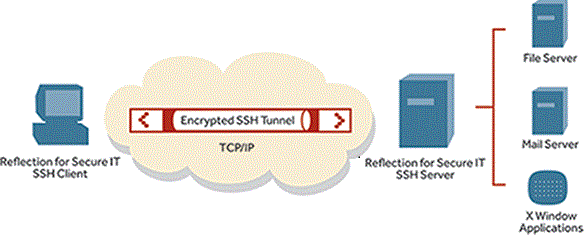
- Access any TCP/IP-based application through a secure transmission tunnel.
Secure internet file transfers
Reflection for Secure IT allows you to confidently exchange private files with business partners and customers over the Internet, so that you can support safer information sharing and meet growing regulatory requirements with confidence.
Convenient, secure administration
With Reflection for Secure IT, you can use interactive access, scripting, and APIs to automate and schedule routine system administration tasks over a secure channel. Reflection for Secure IT also helps boost administrative control. Process Priority allows you to limit the amount of CPU resources consumed to give priority to real-time business critical applications. And with Post Transfer Actions, you can automate important actions for files after they are received, so that business processes run even more smoothly.
Secure application access for users
With Reflection for Secure IT, you can protect the network communications of any TCP/IP- based application.
Secure Shell Access
- Secure remote terminal connections
- Configurable terminal provider (i.e., cmd.exe)
- Configurable terminal default directory
- Use of mapped drives to access network directories during terminal sessions
- Secure remote command execution
Secure File Transfer
- SCP and SFTP version 4 protocol support
- SCP and SFTP special features
- Smart Copy (to eliminate redundant copying of identical source and target files)
- File transfer resume after interrupted downloads
- SCP1 protocol support (for compatibility with OpenSSH clients)
- Virtual directory and chroot environment support
Access Control
- Assignable rights (allow or deny)
- Terminal shell access
- Exec requests
- Local port forwarding
- Remote port forwarding
- SCP1 access
- SFTP/SCP2 access
- SFTP activities (Browse, Download, Upload, Delete, and Rename)
- Assignable to (subconfigurations)
- Global
- Groups
- Users
- Per client system (by IP address or domain name)
- Deny connections to users without Windows interactive access rights
- Control over the number of connections allowed per user
- Use of alternative credentials for accessing SFTP directories (for file transfers) and mapped drives (for terminal sessions)
Tunneling
- TCP port forwarding (local and remote)
- FTP protocol (active and passive mode)
- RDP protocol
Standards Support
- Compliance with IETF Secsh Internet drafts and RFCs 4250–4254, 4256, 4462, 4344, 4345, and 4716
- UTF-8 character support
Cryptographic Library Validation
- FIPS 140-2 validated
Algorithms
- Ciphers
- AES (128-, 192-, and 256-bit CTR)
- AES (128-, 192-, and 256 bit-CBC)
- 3DES (3 56-bit key EDE)
- Blowfish (128-bit)
- CAST (128-bit)
- Arcfour (128- and 256-bit)
- MACs
- HMAC-MD5 (optional MD5 rejection available)
- HMAC-MD5-96
- HMAC-SHA1
- HMAC-SHA1-96
- HMAC-SHA256
- HMAC-SHA512
- RIPEMD160
- Meets DoD requirements for SHA-2
- Key exchange
- Diffie-Hellman
- GSS-API key exchange
Authentication
- Server authentication
- Public key (RSA and DSA)
- PKI X.509 certificates
- GSSAPI/Kerberos
- User authentication
- Password (local user and Windows domain user)
- Public key
- RSA user keys
- DSA user keys
- X.509 certificates
- OpenSSH public key interoperability
- Keyboard interactive
- RSA SecurID
- RADIUS
- Keyboard-interactive password
- GSSAPI/Kerberos
- Reflection PKI Services Manager
- Centralized configuration and management of PKI functions across multiple Reflection for Secure IT Windows servers, UNIX servers, and UNIX clients
- Standalone service module supported on most platforms supported by Reflection for Secure IT Windows and UNIX servers
- DoD PKI certified
- FIPS 140-2 validated for most supported platforms (in process as of July 2013)
- RFCs 2253, 2560, and 3280
- X.509 certificates for server and client authentication (X.509 versions 1-3)
- Version 2 X.509 CRL
- OCSP revocation checks
- HSPD-12 support
- Support for LDAP and HTTP certificate and CRL repositories
- Support for Microsoft Windows Certificate Store
- Certificate extensions supported
- CDP
- IDP
- AIA
- Policy constraints
- Basic constraints
- Name constraints
- Extended key usage
- Customizable configuration on per trust anchor basis
- Fully customizable mapping of SSH user account names to certificates
- SOCKS proxy support
- PKI client command line utility for querying services availability and certificate validity
Auditing and Logging
- Configurable Windows Event Log level
- Configurable Debug Log with local and UTC time stamps
- Notification of exceeded maximum password attempts
- Dedicated audit log for all file transfers
Administrative Tools
- Post Transfer Actions for automating important processes for files after they are received
- ProcessPriority for limiting the amount of CPU resources consumed
- Customizable locations for server configuration files
- Section 508 support in the Reflection for Secure IT Server for Windows configuration utility

