![]() Data Security and SSL Data Encryption
Data Security and SSL Data Encryption
SafeConduct brings benefits of the Secure Sockets Layer/Transport layer Security (SSL/TLS) v3.0 standard, including digital certificate authentication and 256-bit data encryption, to any point-to-point application data traffic.
Many enterprise applications today access sensitive data across the Internet or VPNs without employing data encryption or client authentication. As such, legacy application data traffic is susceptible to unauthorized access or tampering and thus raises serious information privacy and quality risks. SafeConduct transparently removes these risks by securely protecting virtually all application data access without impact to existing applications.
SafeConduct can be used with a variety of application architectures including client-server, host-slave, or multi-tier. Examples include applications accessing databases, file transfer utilities, terminal emulation sessions, email access, or remote monitoring applications. These third-party or in-house developed applications are transparently secured and do not require change to the application source code.
SSL Sta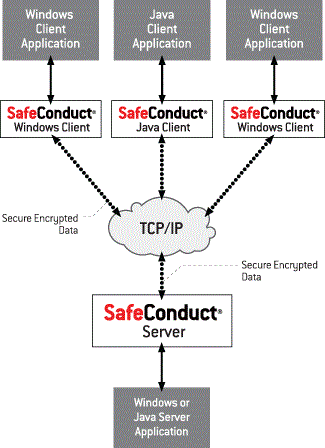 ndard
ndard
SafeConduct delivers the benefits of Secure Sockets Layer/Transport Layer Security (SSL/TLS) v3.0 encryption, including digital certificate authentication and 256-bit data encryption, to your data traffic over VPN or the Internet. The SafeConduct product family transparently works with new and legacy applications. Using SSL, the most widely used protocol for security data transmission on the Internet, SafeConduct eliminates significant risk in information security and privacy.
Secure Channel
SafeConduct builds an invisible, secure channel between two TCP/IP nodes. Before any application data traffic is sent, SafeConduct authenticates the machines, securely negotiates encryption keys, transmits secured user ID/password data, and finally transmits secured application data between the two nodes. SafeConduct prevents unauthorized machines from accessing applications. It also prevents unauthorized access to any application data transmitted over TCP/IP networks.
SafeConduct monitors and intercepts TCP/IP data at pre-configured port addresses. Once secure communication is established between the two TCP/IP nodes, SafeConduct routes application data traffic to the true destination application port address. SafeConduct Server may be installed on a machine other than the one of the server application in order to redirect requirements for SSL encryption processing.
Server and Client for All Platforms
The SafeConduct product family includes the SafeConduct Server, SafeConduct Windows Client, and the SafeConduct Java Client. The SafeConduct Windows client runs on client and server platforms as an application or service. The SafeConduct Java Client and the SafeConduct Server can be used on multiple client and server platforms including, but not limited to, Linux, Solaris, Windows, IBM OS/390 and z/OS, IBM i/iSeries/AS400, IBM AIX, Mac OSX, and OS/2.
| Key Features | Benefits |
| SSL and TLS support – 256 bit encryption | Data protected from unauthorized access |
| NIST FIPS 140-2 validated crypto and SSL functions |
Approved US Government standards |
| Node-to-Node authentication | Assurance that only authorized point-to-point pairs may exchange data |
| No change required to application source code | Protect Investments |
| Broad platform support | Single tool for enterprise deployment |
| Data encryption using the DigitalSignature Standard (DSS), with theDigital Signature Algorithm (DSA) and RSA algorithm |
Standards-based, secure architecture |
| Extensive internal and Windows log reporting and accessibility |
Audit tool for data analysis |
| Graphical tools for certificate generation and management |
Faster administration processing |
| Optional integration with certificates obtained from an external certificate authority |
Flexible support for third-party security |

